We read every piece of feedback, and take your input very seriously.
To see all available qualifiers, see our documentation.
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
https://www.freebuf.com/articles/terminal/205079.html
类似上图,左侧是源码,右侧是加固后脱壳后的dex,但打开是看不到方法体的
The text was updated successfully, but these errors were encountered:
结论:我也不知道。 原因:我还没研究过类似问题。 为何没研究:之前只是工作1个多月涉及到并研究了安卓破解的内容。现在主力工作不是这方面的,现在没机会、没时间继续研究。 只能是:希望以后有时间,我能有机会继续研究这方面。然后相信会研究出一些东西,并能给到你帮助。
Sorry, something went wrong.
@crifan 好的,我也是发个Issue记录下,我有进展也会来更新
需要寻找合适的时机脱壳,一般类似的加固会在调用时机将方法内容回填回去。
对应的就是主动调用式脱壳,即全部方法主动调用收集方法内容。
可以参看时下流行的基于rom定制的fart以及相关衍生工具。
No branches or pull requests
https://www.freebuf.com/articles/terminal/205079.html
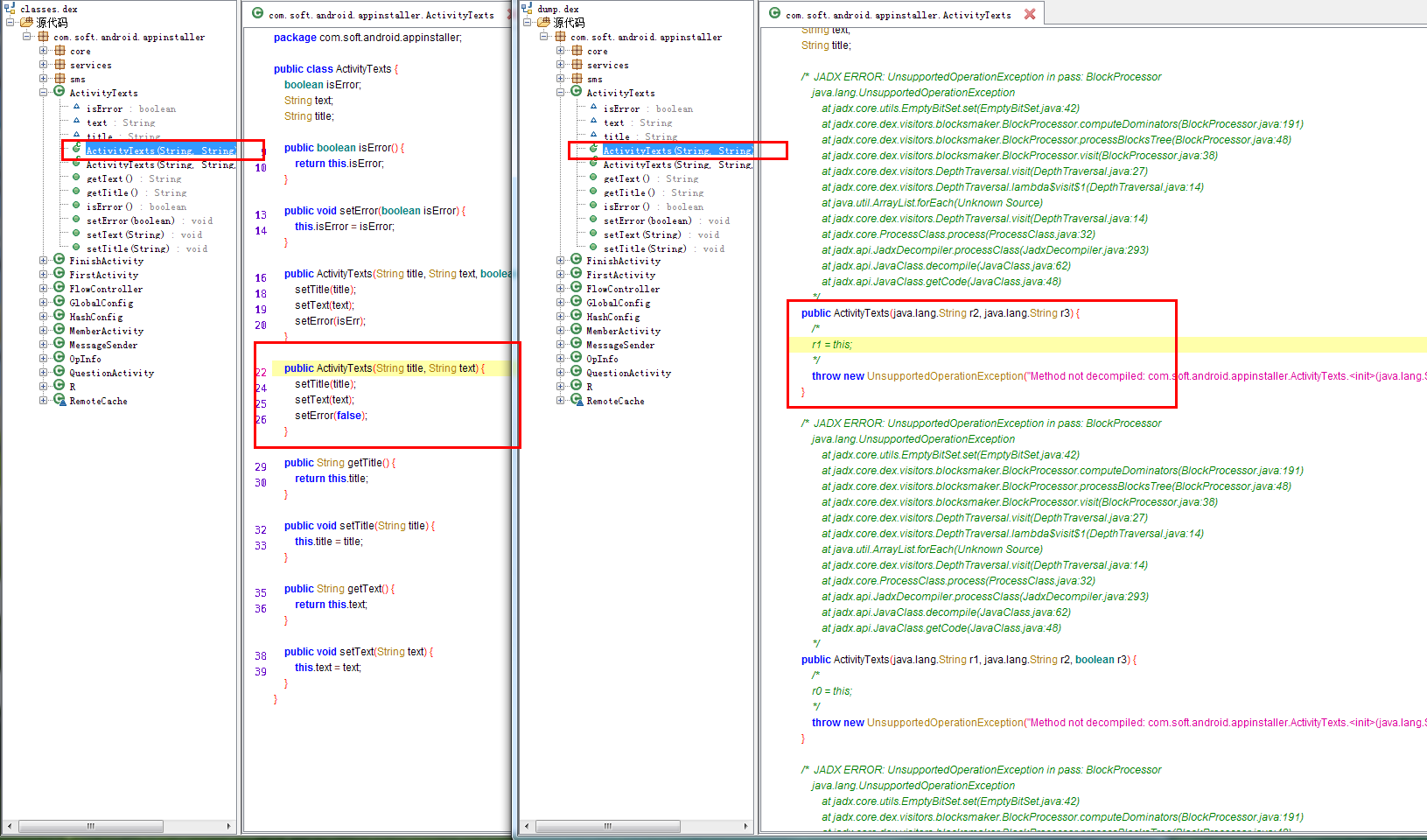
类似上图,左侧是源码,右侧是加固后脱壳后的dex,但打开是看不到方法体的
The text was updated successfully, but these errors were encountered: